Secure MFA at Scale — How We Built Our Own TOTP Provider
In large organizations, employees are constantly joining, leaving, or changing roles. Managing user access manually just doesn't scale — that's why enterprises rely on Identity Management (IDM) systems to automate account creation, deactivation, and access policies.
To strengthen security, most environments also enforce Multi-Factor Authentication (MFA). One of the most common methods is TOTP — time-based one-time passwords that change every 30 seconds and are used in addition to the main password.
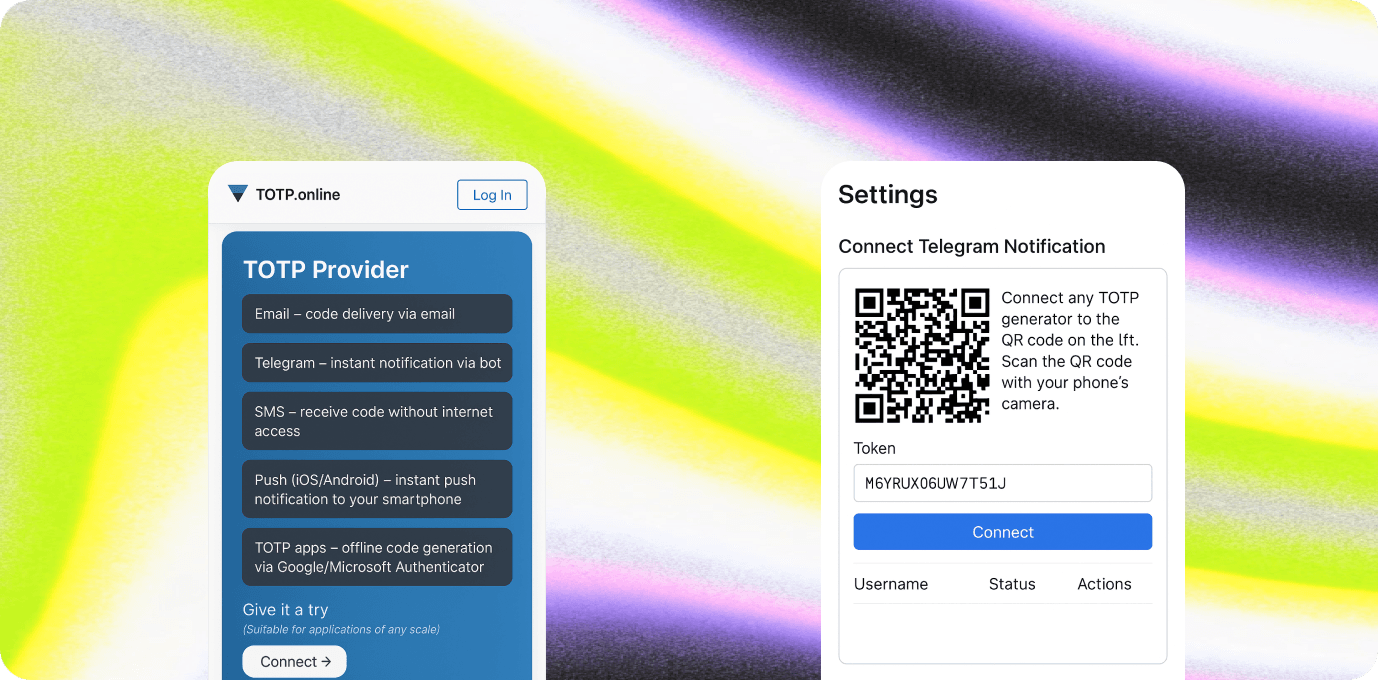
We built TOTP.online as a standalone service that integrates directly into corporate IAM flows. It allows users to register a second factor themselves and receive authentication codes through multiple channels:
- Email — code delivery via email - Telegram — instant bot notifications - SMS — receive codes without internet - Push (iOS/Android) — real-time push messages - TOTP apps — offline code generation via Google or Microsoft Authenticator
This flexibility makes it easy to embed second-factor verification into any internal system — from admin panels to secure portals — while supporting both online and offline use cases.
The service was designed for scalability and infrastructure compatibility. We used:
- Next.js + TypeScript for the web interface and server logic - Telegram Bot API for instant code delivery - Redis for rate limiting and code storage - PostgreSQL for structured data - Docker and GitHub Actions for automated deployments
TOTP.online can be deployed internally, works with any authentication gateway, and is suitable for teams of any size — from startups to enterprise-scale infrastructure. We've also written a detailed article with architecture insights and implementation details.